Simjacker Attack
It is an SMS based attack method. It is a SIM card flaw that lets hackers hijack any phone (independent of the manufacturer) just by sending an SMS. It is called Simjacker because:
- It involves hijacking sim cards.
- Threatens mobile phone users.
This vulnerability resides in in a particular piece of software, called the S@T Browser (a dynamic SIM toolkit), embedded on most SIM cards that requires interaction with the SIM card (e.g. checking bank account balance via the SIM). It is widely being used by mobile operators in at least 30 countries and can be exploited regardless of which handsets victims are using. This technology has not been updated in the past decade still it is present on many sim cards. This is the main reason which provides an easy gateway for hackers to perform this attack. The attack has been tested against phones from Apple, Google, Huawei, Samsung, Motorola and ZTE, and even against some IoT devices that use SIM cards.
S@T Browser, short for SIMalliance Toolbox Browser, is an application that comes installed on a variety of SIM cards, including eSIM, as part of SIM Tool Kit (STK) and has been designed to let mobile carriers provide some basic services, subscriptions, and value-added services over-the-air to their customers. The S@T browser contains a set of STK instructions like: send short message, setup call, launch browser, provide local data and send data. These instructions can be triggered just by sending an SMS to a device and can be easily executed on a mobile phone as well.
The messages sent to the victim includes a hidden Sim Toolkit instruction package that interacts with the S@T Browser. That’s an application residing on the SIM card inside many phones, not on the phone itself. Therefore, none of the security features of Android or iOS is able to block this attack.
How Simjacker attack works?
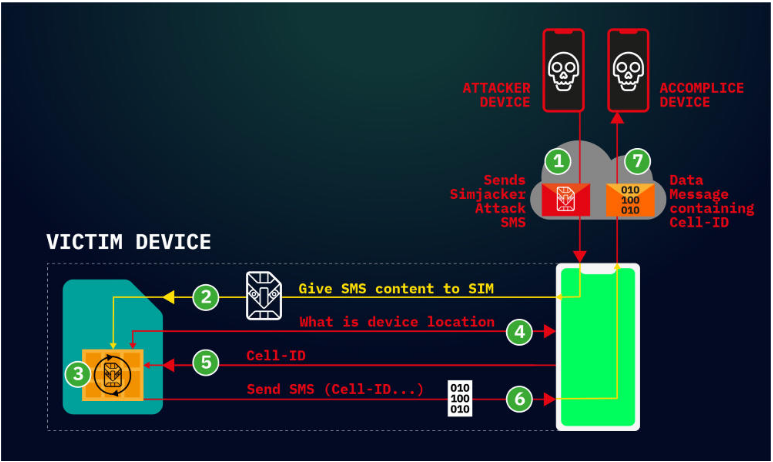
This vulnerability can be exploited using a $10 GSM modem to perform various actions listed below just by sending an SMS containing a spyware-like code:
- Retrieving targeted device’ location and IMEI information.
- Spreading mis-information by sending fake messages on behalf of victims.
- Performing premium-rate scams by dialling premium-rate numbers.
- Spying on victims’ surroundings by instructing the device to call the attacker’s phone number.
- Spreading malware by forcing victim’s phone browser to open a malicious web page.
- Performing denial of service attacks by disabling the SIM card.
- Retrieving other information like language, radio type, battery level, etc.
The Simjacker attack is completely silent. Victims don’t see any SMS messages inside their inboxes or outboxes. This allows threat actors to continuously bombard victims with SMS messages and keep track of their location as they move through the day, week, or month.
Furthermore, because Simjacker exploits a technology residing on the SIM card, the attack also works independently of the user’s device type.
The SIMalliance recommends following security measures:
- Security for S@T push messages: This security can be introduced at two different levels:
- At the network level, filtering can be implemented to intercept and block the illegitimate binary SMS messages
- At the SIM card level, the Minimum-Security Level—MSL—attached to the S@T browser in push mode can force Cryptographic Checksum + Encryption (MSL = 0x06 at least).



