Actively Exploited Windows Kernel EoP Bug Allows Takeover
Introduction:
Microsoft addressed 56 security vulnerabilities for February Patch Tuesday — including 11 critical and six publicly known. And, it continued to address the Zerologon bug.
Microsoft has addressed nine critical-severity cybersecurity bugs in February’s Patch Tuesday updates, plus an important-rated vulnerability that is being actively exploited in the wild.
Six of the security holes – including one of the critical bugs – were already publicly disclosed.
Overall, the computing giant has released patches for 56 CVEs covering Microsoft Windows components, the .NET Framework, Azure IoT, Azure Kubernetes Service, Microsoft Edge for Android, Exchange Server, Office and Office Services and Web Apps, Skype for Business and Lync, and Windows Defender.
What is Zerologon bug:
Microsoft issued an update for a severe bug in its operating system (CVE 2020-1472), which can be used to change any Active Directory account’s password. Easily too, the attack can be scripted to run in less than three seconds. The vulnerability stems from a communications’ protocol that Windows uses to talk back & forth between computers linked together in an Active Directory domain. The protocol itself is essentially undocumented (besides the fact that it exists.) Microsoft used the same approach as the designers of SCADA did, assuming their communications were secure, so long as they remained undocumented.
To ensure communications are secure, there is a cryptographic aspect to all of this. Unfortunately, the cryptography was essentially broken and there are only 256 different combinations possible. From a manual human perspective, this is not difficult; from a machine standpoint, this is essentially worthless.
Now in Active Directory, you can login on any computer. Once you do so, you can do things like change your password. All of this is handled by the same communications’ protocol which sends those logins and password resets back to the Domain Controller for verification. So, pick an account and then fire off 256 different combinations of “Set Password on Account X to BLAH” and there you go.
Within a few seconds you could change the password on any account, without ever having to login in the first place. Once you have an account, get the list of users, and reset everyone’s password. So, in 5 minutes or less, you can lock every user out of the domain and do anything.
What an attacker can do using Zerologon bug:
- The attack only works if it is aimed at the Domain Controller
Patch for Zerologon bug:
The patch corrects the problem in a couple of ways: First, it fixes the whole cryptographic issue (no more 256 possible combinations garbage.) Second, there is now an event log created when a communications attempt is rejected. So not only is the hole fixed, but you can tell if someone is trying to actively exploit it. The patch is available for the following Windows Server operating systems:
- 2008 SP 1
- 2012
- 2012 R2
- 2016
- 2019
- Server Version 1903, 1909 & 2004
Affected CVE:
- CVE-2021-1732
- CVE-2021-26701
- CVE-2021-1722
- CVE-2021-24077
- CVE-2021-24074
- CVE-2021-24094
- CVE-2021-24091
- CVE-2021-24078
- CVE-2021-24112
- CVE-2021-24081
- CVE-2021-1733
- CVE-2020-1472
Latest Count
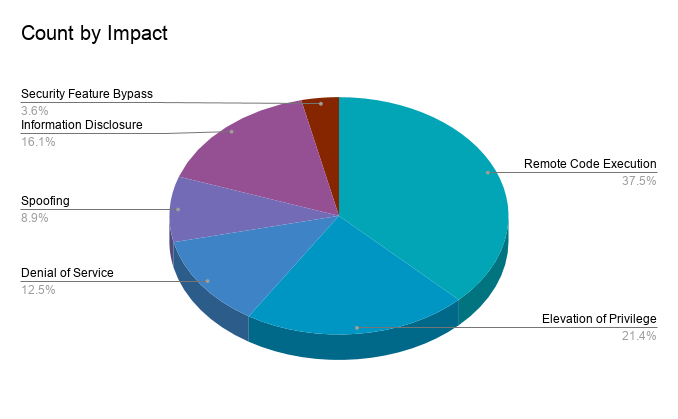 Critical Microsoft Bugs for February Patch
Critical Microsoft Bugs for February Patch
None of the critical bugs rate more than an 8.8 (out of 10) on the CVSS scale, but all allow for remote code execution (RCE) and many should take top priority, according to security researchers.
- The bug tracked as CVE-2021-1732 is being actively exploited, according to Microsoft’s advisory. It carries a vulnerability-severity rating of 7.8 on the CVSS scale, making it important in severity – however, researchers said it deserves attention above some of the critical bugs in terms of patching priority. “The vulnerability affects Windows 10 and corresponding server editions of the Windows OS, “This is a prime example of why risk-based prioritization is so important. If you base your prioritization off of vendor severity and focus on ‘critical’ you could have missed this vulnerability in your prioritization. This vulnerability should put Windows 10 and Server 2016 and later editions into your priority bucket for remediation this month.”
- The bug tracked as CVE-2021-26701 exists in .NET Core and Visual Studio – it’s the only critical-rated bug to be listed as publicly known.
- The bugs tracked as CVE-2021-1722 and CVE-2021-24077 meanwhile are both Windows Fax Service RCE problems. “Windows Fax Service specifies settings for faxes, including how they are sent, received, viewed and printed,” said Eric Feldman, senior product marketing manager at Automox. “The Windows Fax Service is used by the Windows Fax and Scan application included in all versions of Microsoft Windows 7, Windows 8 and Windows 10 and some earlier versions.”
- CVE-2021-24074 and CVE-2021-24094 are both Windows TCP/IP RCE vulnerabilities. The former is found in the way Windows handles iPv4 source routing; the latter is found in the way Windows handles iPv6 packet reassembly. “IPv4 source routing should be disabled by default, “You can also block source routing at firewalls or other perimeter devices. The IPv6 bug involves packet fragmentation where a large number of fragments could lead to code execution.”
- Windows Camera Codec Pack is home to yet another critical RCE bug (CVE-2021-24091). If successfully exploited, an attacker could run arbitrary code in the context of the current user.
- Windows Domain Name System (DNS) servers, when they fail to properly handle requests, are also open to a critical RCE bug (CVE-2021-24078) that could allow an attacker to run arbitrary code in the context of the Local System Account.
- CVE-2021-24088 affects the Windows Local Spooler, which is an important component within the Windows operating system that stores print jobs in memory until the printer is ready to accept them. It’s a bug that “could be a big concern,” according to Allan Liska, senior security architect at Recorded Future.
- .NET Core for Linux is also at risk for RCE (CVE-2021-24112) and CVE-2021-24093 is a critical RCE vulnerability in the Windows graphic component. Details are scant for both, but of the latter, Breen said, “This is the kind of vulnerability built into exploit kits and triggered by low level phishing campaigns targeting users.”
- And, a critical bug that would allow RCE exists in the Microsoft Windows Codecs Library (CVE-2021-24081). Details are sparse, but Microsoft said that the difficulty required for exploitation is considered to be low. However, end-user interaction is required for successful exploitation.
- Outside of the critical issues, CVE-2021-1733 is a high-severity EoP vulnerability discovered to be impacting Sysinternals PsExec utility that deserves a look. It’s listed as being publicly disclosed.
Remediations
- Update Your Windows OS. (February Patch)
- For CVE-2021-1732: A complete vendor solution is available. Either the vendor has issued an official patch, or an upgrade is available.
- CVE-2021-26701 officially fix by Microsoft.
- Remaining all the CVE Fixed by Microsoft.
- Tools like PsExec it is important to understand your software inventory and where these tools are installed and ensure you can distribute updated versions as needed.



