Indian Power Company targeted by Pakistan-linked Hackers
According to the research Lumen’s Black Lotus Labs detected a new remote access trojan called ReverseRat. The attackers are suspected ties to Pakistan which are making themselves noticeable to government and energy organizations in the South and Central Asia regions to deploy a remote access trojan on compromised Windows systems.
Lumen’s Black Lotus Labs said in the analysis that “Most of the organizations that exhibited signs of compromise were in India, and a small number were in Afghanistan. The potentially compromised victims aligned with the government and power utility verticals.”
Lumen suspects Pakistan state-sponsored actors are likely behind this campaign, which is said to have begun in January 2021. The potentially compromised victims aligned with the government and power utility verticals. Some of the victims also include a foreign government organization, a power transmission organization, and a power generation and transmission organization.
Along with ReverseRat, threat actors also deployed an open-source RAT known as AllaKore to compromise targeted machines and obtain access.
Technique
There are number of reasons that highlighted the intrusion:
- Due to its highly-targeted nature,
- The tactics, techniques, and procedures (TTPs) adopted by the adversary rely on repurposed open-source code and the use of compromised domains in the same country as the targeted entity to host their malicious files.
- Are attentive to hide their activity by modifying the registry keys, granting them the ability to surreptitiously maintain persistence on the target device without attracting attention.
A multi-step infection chain was observed by Lumen, noted that the campaign “resulted in the victim downloading two agents; one resided in-memory, while the second was side-loaded, granting threat actor persistence on the infected workstations.”
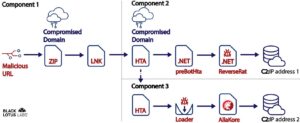
The attack is initiated by a malicious link sent via phishing emails or messages, which is when clicked downloads a ZIP archive file containing a Microsoft shortcut file (.lnk) and a decoy PDF file from a compromised domain. The zip file then deploys two HTA files named CactusTorch and preBotHta, which contain malicious JavaScript code.
The decoy PDF documents associated with this larger describe the activity referred to organizations and events relevant to India in spring 2021. Some of the decoy documents, or lures, were more generic, making references to disguising as a user manual for registering and booking an appointment for COVID-19 vaccine through the CoWIN online portal, while a few others masquerade as the Bombay Sappers, a regiment of the Corps of Engineers of the Indian Army.
A JavaScript code-based GitHub project CactusTorch is leveraged to inject a 32-bit shellcode into a running process to ultimately install a .NET backdoor called ReverseRat that runs the typical spyware gamut, with capabilities to capture screenshots, terminate processes, execute arbitrary executables, perform file operations, and upload data to a remote server.
The researchers said that, “While this threat actor’s targets have thus far remained within the South and Central Asian regions, they have proven effective at gaining access to networks of interest. Despite previously relying upon open-source frameworks such as AllaKore, the actor was able to remain effective and expand its capabilities with the development of the Svchostt agent and other components of the ReverseRat project.”
Remediation
In order to prevent, Black Lotus Labs null-routed the threat actor infrastructure across the Lumen global IP network and notified the affected organizations. Black Lotus Labs continues to follow this threat group to detect and disrupt similar compromises, and they encourage other organizations to alert on this and similar campaigns in their environments.
Lumen advise security practitioners to learn the threat actor’s current tactics, tools and procedures to better defend their organizations against potential attacks.



