Dropbox discloses breach after hacker stole 130 GitHub repositories
The cloud storage provider Dropbox disclosed a recent phishing attack targeting the company’s employees that resulted in unauthorized access to 130 of its GitHub repositories after gaining access to a GitHub account using employee credentials obtained in a phishing attack. The cloud giant said it discovered the breach on October 14 when GitHub notified it of suspicious activity that started the previous day. The multiple Dropboxers received phishing emails impersonating CircleCI, with the intent of targeting our GitHub accounts.
The company’s security team stated that these stolen repositories included “some credentials—primarily, API keys—used by Dropbox developers”. The code and the data around it also included a few thousand names and email addresses belonging to Dropbox employees, current and past customers, sales leads, and vendors (for context, Dropbox has more than 700 million registered users). The company has notified all those affected by this data breach.
The successful breach resulted from a phishing attack that targeted multiple Dropbox employees using emails impersonating the CircleCI continuous integration and delivery platform and redirecting them to a phishing landing page where they were asked to enter their GitHub username and password.
On the same phishing page, the employees were also asked to “use their hardware authentication key to pass a One-Time Password (OTP) to the malicious site.”
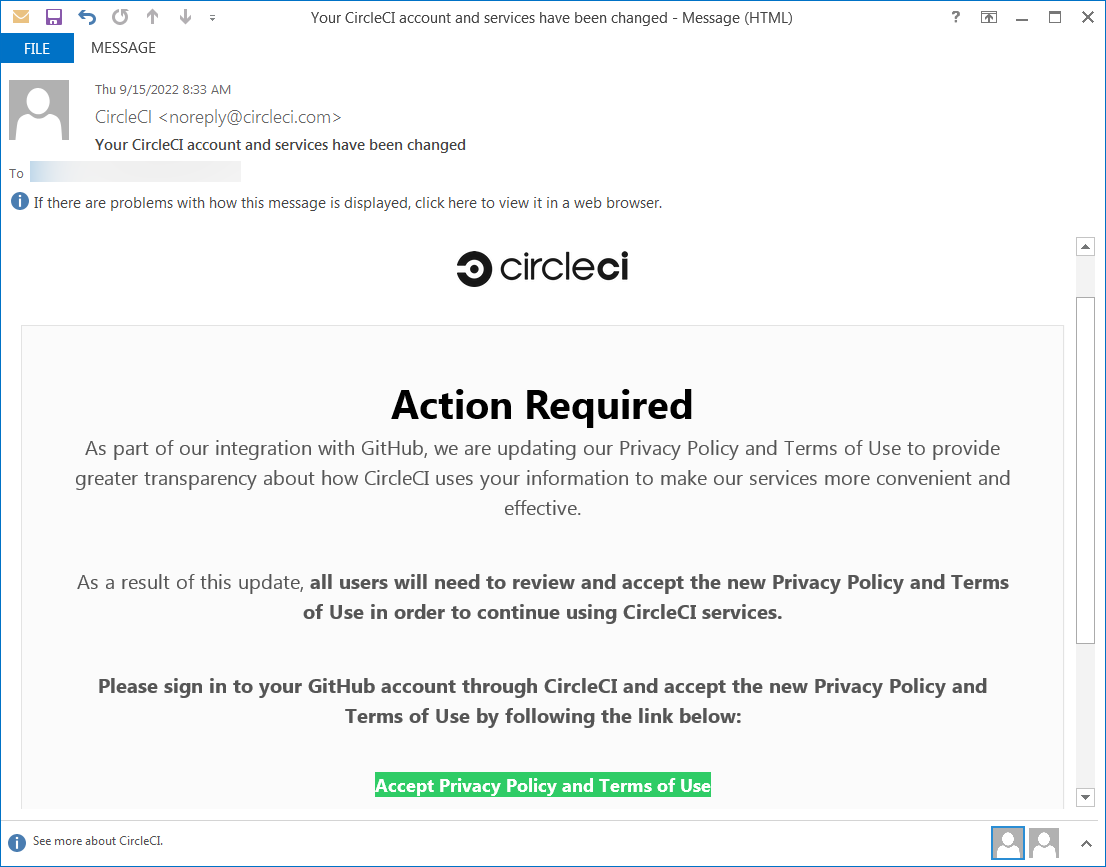
After stealing the Dropboxers’ credentials, the attackers gained access to one of Dropbox’s GitHub organizations, where they proceeded to copy 130 of their code repositories.
These repositories included our own copies of third-party libraries slightly modified for use by Dropbox, internal prototypes, and some tools and configuration files used by the security team,” the company added. Dropbox added that the attackers never had access to customers’ accounts, passwords, or payment information, and its core apps and infrastructure were not affected as a result of this breach. Dropbox is working on securing its entire environment using WebAuthn and hardware tokens or biometric factors.
“While GitHub itself was not affected, the campaign has impacted many victim organizations,” GitHub said in an advisory at the time.
GitHub said it detected content exfiltration from private repositories almost immediately after the compromise, with the threat actors using VPN or proxy services to make tracing them more difficult.
Remediation:
- Conduct continuous scheduled training sessions for the employees with mock phishing scenarios.
- Deploy a SPAM filter that detects malwares, blank senders, etc.
- Keep all systems current with the latest security patches and updates.
- Install an antivirus solution, schedule signature updates, and monitor the antivirus status on all equipment.
- Develop a security policy that includes but isn’t limited to password expiration and complexity.
- Deploy a web filter mechanism to block malicious website.
- Encrypt all sensitive company information at rest with the proper backup suites.
- Implement email encryption for employees that are telecommuting.



