Security Threats on Recycled Phone Numbers
Nowadays the users with recycling mobile phone numbers falling into the trap of attackers. A new academic result stated that the security and privacy of recycling mobile phone numbers are at high-risk stake. They can be made victim of many kinds of exploit which can be account takeovers, phishing or spam attacks, and can even restrict the access of victims from signing up for online services or platforms. A phone number recycling is a method in which the disconnected phone numbers were reassign to new customers by their service providers.
The research stated that around 66% of recycled phone numbers were linked to their previous owner’s online accounts at various popular websites. This can potentially lead to hijacking the accounts by simply recovering the accounts who are linked with those recycled numbers. An attacker can simply get the numbers, use them to reset the passwords on existing accounts, as the OTP is sent via SMS, it can be received and entered correctly.
“An attacker can cycle through the available numbers shown on online number change interfaces and check if any of them are associated with online accounts of previous owners,” the researchers said. “If so, the attacker can then obtain these numbers and reset the password on the accounts, and receive and correctly enter the OTP sent via SMS upon login.”
How research was conducted?
The research was conducted in the form of survey of 259 phone numbers that were new subscribers available to telecom majors T-Mobile and Verizon Wireless in the United States. The research was conducted by the two individuals Kevin Lee of Princeton University and Prof. Arvind Narayanan who is a member of the Center for Information Technology Policy’s executive committee.
According to the Federal Communications Commission (FCC), it was highlighted that around every year as an estimated value, 35 million phone numbers in U.S. are disconnected. Due to this, attacker tries to perform reverse lookup by entering some certain numbers randomly in different online websites offered by the two carriers. When they get hold with the recycled number, they buy those numbers and make them in use to get the access in different victim’s account in which the recycled number is linked.
The attackers make this attack successful due to the lack of restrictions of query which is made for the available numbers appointed by the carriers on their prepaid interfaces to change numbers. In addition to displaying “full numbers” it gives an attacker an opportunity or an advantage to discover the recycled numbers before verifying a number change.
The research also states the proof that authentication which is based on SMS is now a risky method. The attacker can hijack an SMS 2FA-enable account without having the knowledge of the password.
According to Narayan’s tweet, “If you need to give up your number, unlink it from online services first. Consider low-cost number ‘parking’ services. Use more secure alternatives to SMS-2FA such as authenticator apps.”
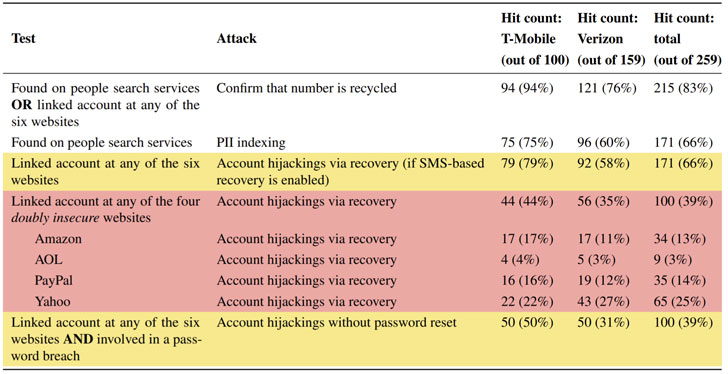
Out of those sampled phone numbers 100 were already involved in a data breach in the past as their numbers were associated with the email addresses, by allowing account hijacks of a second kind that circumvent SMS-based multi-factor authentication. In third attack, out of 259, 171 numbers were listed on people search services like BeenVerified and due to that the sensitive personal information of the owners were leaked in the process.
“Once they obtain the previous owner’s number, they can perform impersonation attacks to commit fraud or a mass even more PII on previous owners,” the researchers explained.
Apart from the reverse lookup attacks, there were five additional threats that were identified by targeting the previous and future owners of recycled numbers. It allows the malicious attack to impersonate the past owners and hijack the victims online account with phone numbers and other linked online accounts, which can at worst carry out denial-of-service attacks by the attacker.
“Attacker obtains a number, signs up for an online service that requires a phone number, and releases the number,” the researchers said. “When a victim obtains the number and tries to sign up for the same service, they will be denied due to an existing account. The attacker can contact the victim through SMS and demand payment to free up the number on the platform.”
Remediation
The response of T-Mobile gave that it has updated its “Change your phone number” support page with information about reminding users to “update your contact number on any accounts that may have your number saved, such as notifications for bank accounts, social media, etc.” and specify the FCC-mandated number aging period of 45 days to allow reassignment of old numbers.
Another telecommunication company Verizon had made similar changes to its “Manage Verizon mobile service” support page. But none of the carriers have made it hard for the attackers to stop them from exploiting the recycled numbers.



