How to Avoid the Top Three Causes of Data Breaches in 2019
Measures to protect the data from:
- Misconfigured Cloud Storage
- Unprotected Code Repositories
- Vulnerable Open Source Software
Misconfigured Cloud Storage: Many companies use cloud servers to store their data. Despite their great advantage, misconfigured servers may expose sensitive data, a mistake which is an open invitation to hackers to dump and use a company’s data for their malicious activities.
Cloud service providers try to improve their cyber resilience as much as possible. They regularly publish best practices on how to use their cloud services in the best possible way and provide options to keep the data public or private as suitable by the organization. Any misconfiguration may expose data to the public and first ones notice these exposed data would be hackers and hacktivists. It is no wonder that Security Misconfiguration is #6 in OWASP Top 10.
Common misconfigurations found are:
- Use of factory default system credentials (username/passwords).
- Directory and file listings that are not disabled and easily available through search engines.
- Some user traces may have too much information such as pages returned to users with error messages.
- Leaving some unnecessary pages such as sample apps, old privileges, and user accounts.
- Not up-to-date software, use of legacy systems, not up-to-date patches.
Some of the major incidents which took place due to this vulnerability:
- A misconfigured Amazon S3 bucket exposed GoDaddy’s critical data on 31,000 GoDaddy servers including architectural details about GoDaddy, high-level configuration information of many systems and pricing facilities for operating those systems such as the discounts offered to customers.
- A cloud data storage contractor for Universal Music Group, Agilisium, created two unprotected instances of the Apache Airflow server that exposed UMG’s internal FTP credentials, AWS Secret Keys and Passwords, the internal and SQL root password to the open internet.
- Honda Car India’s two public unsecured AWS storage sets contained names, phone numbers and emails for both users and their trusted contacts, passwords, gender, information about their cars including VIN, Connect IDs and more. All these sensitive data on these misconfigured servers were exposed to public for more than a year.
Unprotected Code Repositories: Code repositories, such as GitHub, possess potential security issues that users should be aware of. Developers who post work on these sites have put private files into their repositories, which are then copied into public repositories and made searchable. Attackers very well know how easily open source code can be used. They monitor repositories to see who contributes code and which are identified as problematic.
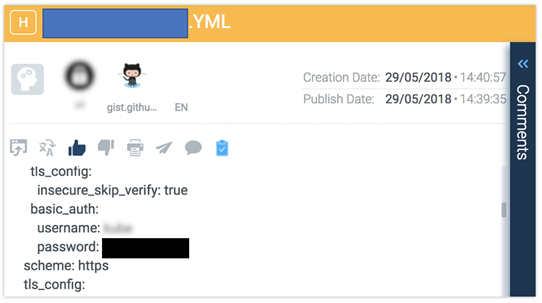
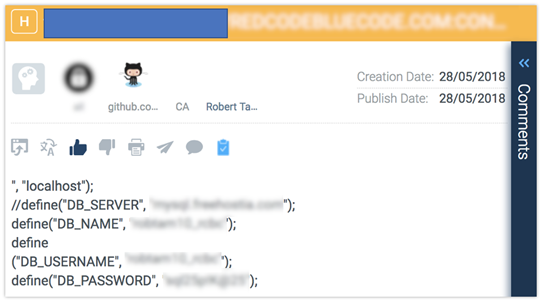
Examples of leaked user credentials on Git-Hub found by CyberInt’s Argos™ platform. The potential threat of data leakage is immense with over 28 million Git-Hub users as of June 2018.
The individual code repositories can sometimes be considered of low importance, but when combined with active reconnaissance techniques, the data can be leveraged in targeted attacks against employees such as:
- Spear phishing campaigns
- Locating potential targets for attack
- Social engineering
- Credential theft
Vulnerable Open Source Software: organizations take advantage of many open source products like code libraries, operating systems, software and applications for various purposes.
What are open source vulnerabilities?
These are like exploits which appear in the proprietary products. These are bits of code that the author accidentally wrote. This can leverage hackers from features that let them to modify the code and use it in a way that was not planned by the author of that code. It can result in attacks like:
- DoS (Denial of Service)
- Taking a service offline
- Remote access to the system.
Some of the Open Source Security Risks and Vulnerabilities to Be Aware Of:
- Public Nature of exploits: In open source projects code is available to anybody. This has its advantages, as people within the open source community can mark potential exploits they identify in the code, which gives open source team leaders time to repair the issue before they publicly announce information on vulnerabilities. However, in time all exploits become public information on the National Vulnerability Database (NVD). Hackers can access this information and go after organizations that are slow to patch an application reliant on open source projects with vulnerabilities.
- Malpractice of developers: developer’s malpractices including copy and pasting code from open source libraries. Copying and pasting are problematic as developers copy any vulnerabilities that could exist in the code of the project when they do it.
Prevention and Remediation:
- Maintain an UpToDate and concise inventory of digital assets: Software, hardware, data, users, and licenses should be continuously monitored, classified, and risk-scored. In the era of public cloud, containers, code repositories, file-sharing services, and outsourcing, it’s not an easy task, but without it, you may ruin the integrity of your cybersecurity efforts and negate all previous cybersecurity investments. Remember, you cannot protect what you don’t see.
- Monitor cyber risk of your 3rd and 4th party providers.
- Regularly check Intrusion Detection System (IDS) logs and consider host-based IDS rather than network-based IDS to examine events on host-level.
- Increase the cyber security awareness of your employees and regularly check for leaked credentials.
- Keep an eye on Dark Web and monitor data leaks: most companies do not realize how many of their corporate accounts, exposed by hacked third-party websites and services, are being sold on the Dark Web. The emerging success of password reuse and brute-force attacks stem from it. Worse, even legitimate websites such as Pastebin often expose a great wealth of leaked, stolen, or lost data accessible to everyone. Continuous monitoring and analysis of these incidents may save millions of dollars and, most importantly, your reputation and goodwill.



