Flaw in Sudo Enables Non-Privileged Users to Run Commands as Root
A vulnerability has been discovered in Sudo which is one of the most important, powerful, and commonly used utilities that comes as a core command installed on almost every UNIX and Linux-based operating system.
Sudo, stands for “superuser do,” is a system command that allows a user to run applications or commands with the privileges of a different user without switching environments most often, for running commands as the root user. Root is the user name or account that by default has access to all commands and files on a Linux or other Unix-like operating system. It is also referred to as the root account, root user and the superuser.
Vulnerability: Sudo security policy bypass issue that could allow a malicious user or a program to execute arbitrary commands as root on a targeted Linux system even when the “sudoers configuration” explicitly disallows the root access. This bug is able to give users almost unlimited access. Ordinarily, in order to execute a Sudo (super user do) command, a user would either have to have been granted the relevant permissions, or would need to know the password for root.
By default, on most Linux distributions, the ALL keyword in RunAs specification in /etc/sudoers file, as shown in the screenshot, allows all users in the admin or sudo groups to run any command as any valid user on the system.
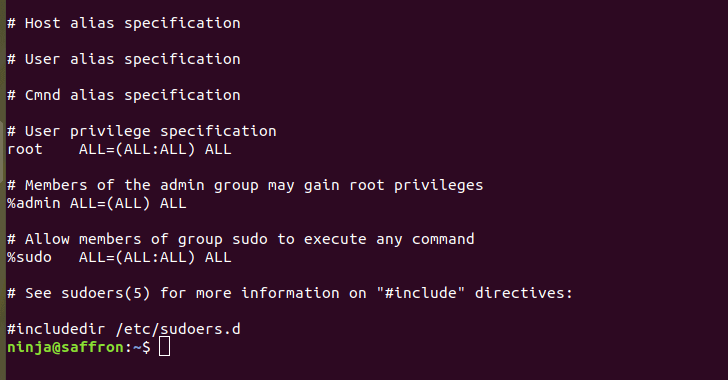
In Linux, separation of privileges is one of the fundamental security paradigms. Administrators can configure a sudoers file to define which users can run what commands as to which users.
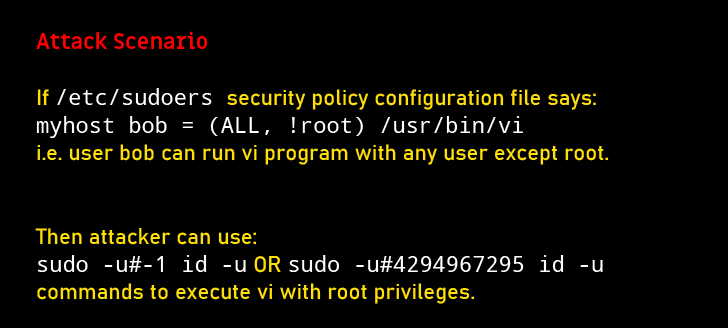
So, in a specific scenario where a specific user has been allowed to run a particular, or any, command as any other user except the root, this vulnerability will still allow you to bypass this security policy and take complete control over the system as root.
“This can be used by a user with sufficient sudo privileges to run commands as root even if the Runas specification explicitly disallows root access as long as the ALL keyword is listed first in the Runas specification,” the Sudo developers say.
CVE ID: CVE-2019-14287
Discovered By: Joe Vennix of Apple Information Security
How to exploit: this flaw can be exploited by an attacker to run commands as root just by specifying the user ID “-1” or “4294967295.” This is because the function which converts user id into its username incorrectly treats -1, or its unsigned equivalent 4294967295, as 0, which is always the user ID of the root user.
Affected Sudo versions: The vulnerability affects all Sudo versions prior to the latest released version 1.8.28.
Remediation: it is recommended to update sudo package to the latest version as soon as it is available.



