New ‘Cheers’ Linux ransomware designed to infect VMware ESXi machines
In the cybercrime world, a new ransomware called ‘Cheers’ has emerged, and it has begun its activities by targeting weak VMware ESXi systems.
Ransomware families like LockBit, Hive, and RansomEXX have targeted ESXi in the past as well.
VMware ESXi, a bare-metal hypervisor, is a virtualization platform utilised by a wide range of enterprises throughout the world. Some well-known cybercriminal gangs have leveraged the compromise of ESXi servers as a means of quickly spreading ransomware to a large number of devices. “It can house dozens of virtualized machines, increasing its prominence in a business’s IT environment and thus greatly increasing the likelihood that an organisation will pay the ransom to restore their servers,” Rosen told The Register.
According to Trend Micro researchers, the ransomware, dubbed “Cheers” or “Cheerscrypt,” hijacks an ESXi server, then starts an encryptor that locates virtual machines and terminates them using an esxcli command.
Infection and encryption
The Cheers ransomware searches for files ending in.log,.vmdk,.vmem,.vswp, and.vmsn. Snapshots, log files, swap files, paging files, and virtual discs are all associated with these file formats in ESXi.
The “.Cheers” extension will be attached to the filename of each encrypted file. Renaming files occurs before encryption, which means that if access permission to rename a file is refused, the encryption will fail but the file will still be renamed.
The encryption approach generates a secret (SOSEMANUK stream cypher) key from a pair of public and private keys and embeds it in each encrypted file. To prevent recovery, the private key used to generate the secret key is deleted.
When the encryption is complete, the ransomware shows statistics about what it has done, including the number of encrypted files and those it didn’t encrypt, as well as the amount of encrypted data.
The ransomware will write ransom notes named ‘How To Restore Your Files.txt’ in each folder while scanning for files to encrypt.
These ransom notes contain details on the victim’s files as well as links to the ransomware operation’s Tor data leak sites and ransom negotiation sites.
Each victim has their own Tor site for discussions, but the Onion URL for the data leak site is static.
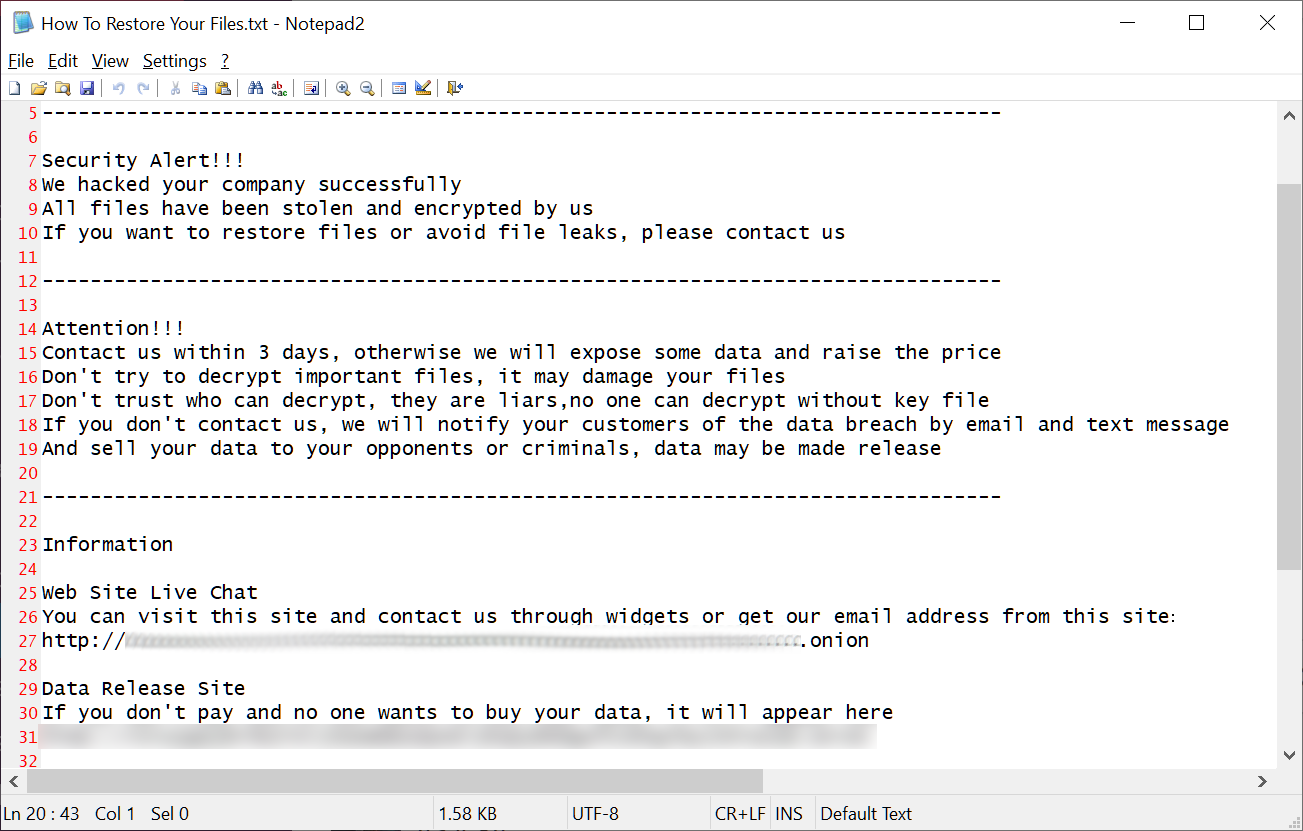
ransom note to victims (source: bleeping computer)
File scrambling process according to ‘trend’ is described below:
It uses Linux’s /dev/urandom to produce an ECDH public-private key pair for each file to encrypt. It then generates a secret key using its embedded public key and the created private key, which will be used as an SOSEMANUK key. It will append the created public key to the encrypted file after it has been encrypted. Because the created private key is not preserved, the embedded public key cannot be combined with the generated private key to generate the secret key. As a result, decryption is only possible if the private key of the malevolent actor is known.
Best practices to prevent your organization from ransomware attacks:
- Make a complete backup of data – Company’s data should be backed up on a regular basis. If something goes wrong, one should be able to revert to a recent backup fast and efficiently. However, if your organization is ever attacked, the consequences will be far less severe.
- Keep software up to date – By exploiting any flaws, ransomware attackers can sometimes gain access to software. Adopt a patch management approach and make sure that everyone on your team is always up to date.
- Enhance threat detection – Before it’s too late, most ransomware attacks may be discovered and resolved. Have an automatic threat detection system in place to increase chances of being protected.
- Multi-factor authentication should be used – Before being granted access to a system, multi-factor authentication requires users to prove their identities in numerous ways. If a criminal obtains an employee’s password, the attacker will be unable to gain easy access to the systems.
- Make use of the least privilege principle – Employees should never have greater data access than they require. Segmenting the company and restricting access can operate as a quarantine, reducing the impact of a possible attack and limiting access vectors.
- Examine and track email and file activity – Cybercriminals using phishing techniques frequently use emails as their primary method of communication. Continuously scan and monitor emails, and consider using an automated email security solution to prevent hazardous emails from reaching users. Consider scanning and tracking file activity as well.
- Employee training should be improved. The majority of ransomware assaults are the result of poor employee behavior or outright carelessness. Someone may give out their password or download an unexpected material on their own volition.
- Don’t pay the ransom – Don’t pay the ransom if your company is the victim of a ransomware assault. It may appear appealing to get out of this difficult circumstance as soon as possible. However, even after that, there’s no guarantee that attacker will be stick to his words.
- Anti-ransomware software should be used – Ransomware must undertake unusual behaviors, such as opening and encrypting massive numbers of files, in order to fulfil its goal. A specialized security solution is required to protect against ransomware that “slips through the cracks.”



