
What is Forensics Analysis?
It is a branch of Digital Forensics. The main purpose of a forensic analysis is to analyze, recover, document and preserve evidence in an investigation. This movement and benefit moreover incorporates a careful investigation of the occurrence and utilizes overviews to accumulate total information of how the breach or information misfortune happened by evaluating the cause and effect.

Applicability
A digital forensic investigation can help you answer any questions you might have about the attack including:
- What networks, systems, files, or applications were affected?
- How did the incident occur? (What tools and attack methods were used, vulnerabilities exploited)
- What data and information was accessed or stolen?
- Are hackers still on my network? (Is the incident finished or is it ongoing?)
Where did the attack come from?
Objective
Thorough Analysis
- It helps to recover, analyse, and preserve computer and related materials in such a manner that it helps the investigation agency to present them as evidence in a court of law.
- It helps to postulate the motive behind the crime and identity the main culprit.
- Designing procedures at a suspected crime scene which helps you to ensure that the digital evidence obtained is not corrupted.
- Data acquisition and duplication: Recovering deleted files and deleted partitions from digital media to extract the evidence and validate them.
- Helps you to identify the evidence quickly, and also allows you to estimate the potential impact of the malicious activity on the victim
- Producing a computer forensic report which offers a complete report on the investigation process.
- Preserving the evidence by following the chain of custody.
Approach
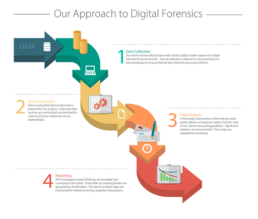
It uses the following steps:
- Identification:
- Identify the purpose of Investigation.
- Identify the resources required.
- Preservation:
- Data is isolate, secure and preserve.
- Analysis:
- Identify tools and techniques to use.
- Process data.
- Interpret analysis results.
- Documentation:
- Documentation of the crime scene along with photographing, sketching, and crime scene mapping.
- Presentation:
- Process of summarization and explanation of conclusions is done with the help to gather facts.
Why CyberSRC®?
Established in January 2018, CyberSRC Consultancy offers the full machination of cyber security services ranging from threat intelligence, VMS to general advisory services in areas pertaining to Cyber security such as vulnerability attacks, compliance, and cyber security regulations, and laws. We are into system audits such as ISNP Audits, NBFC Audits, UCB Audits, PPI Audits, and SEBI Audits. We provide our solutions with better accountability. We are a certified assurance firm. We are an ISO 27001 certified organization, backed by a very diverse and dynamic team which have a combined experience.
